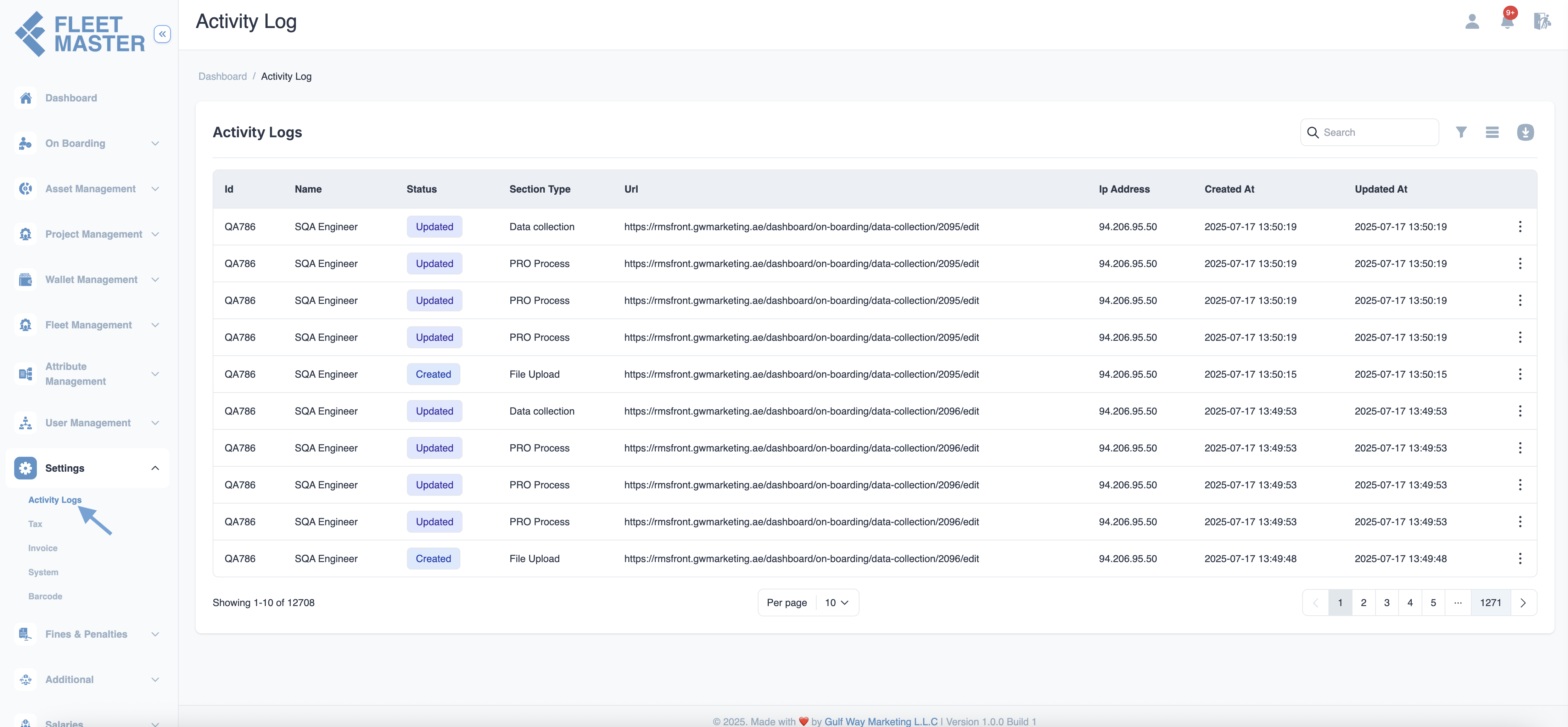
Activity Logs
Track and audit user activity across the system using the Activity Logs feature in fleet master.
Overview
The Activity Logs section in Fleet Master provides a detailed record of user actions across the system, allowing administrators to monitor changes, updates, and access behavior in real time.
Each action entry includes:
- User ID and Name
- Action Type (Created, Updated, Deleted)
- Section Type (Admin, Vehicle, User, etc.)
- URL of the action performed
- IP Address
- Timestamps (Created At, Updated At)
Purpose:
Activity Logs help maintain accountability and transparency across your organization.
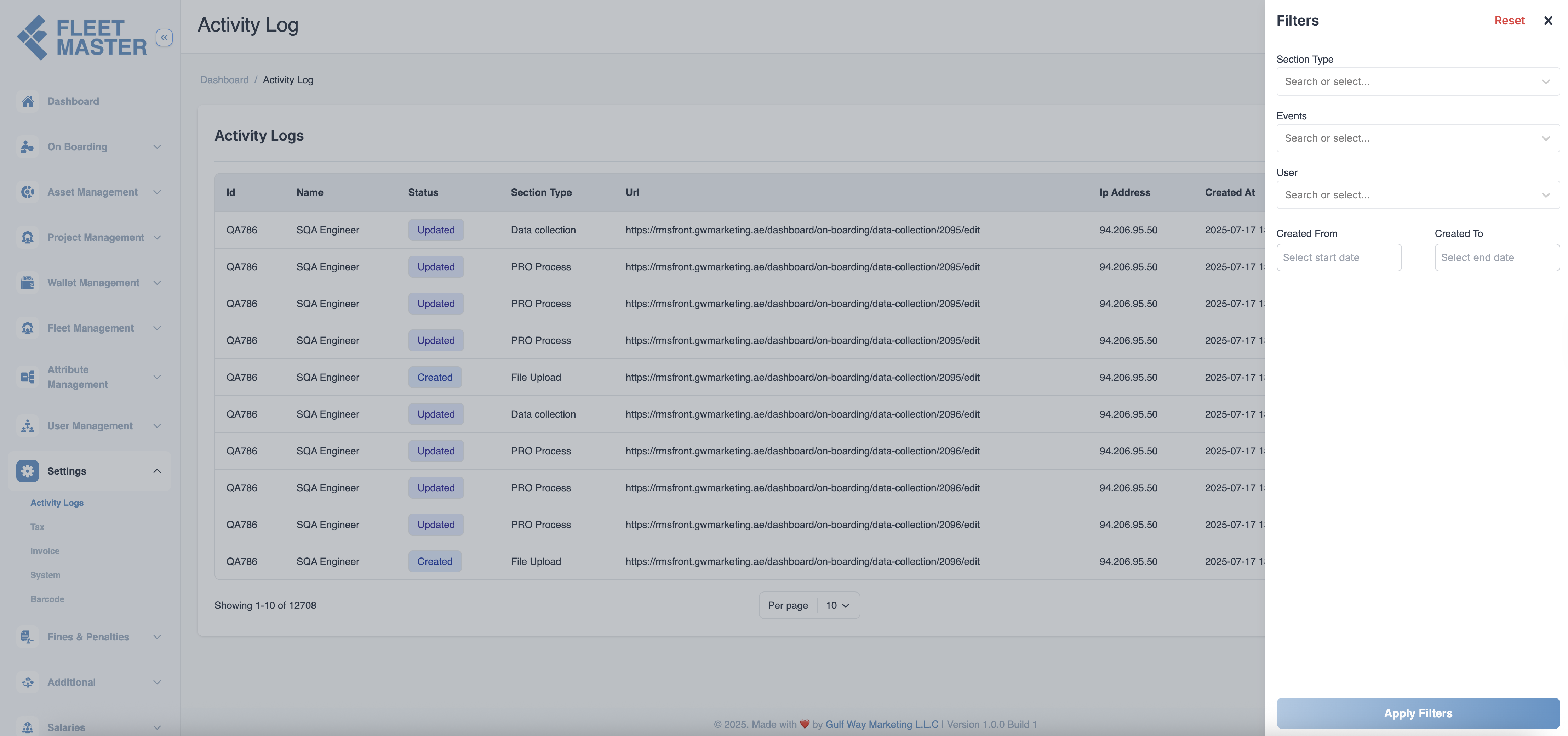
Filtering Logs
You can apply advanced filters to narrow down the activity records:
- Filters: Click the
Filtersbutton to filter by:- Date range
- Status (Created / Updated / Deleted)
- Section Type (Admin, Vehicle, Users, etc.)
- Columns Visibility: Show or hide columns like IP address, timestamps, or URLs as needed.
Exporting Logs
Click the Export button to download the activity logs as a csv or excel file for auditing or compliance needs.
Security Tip:
Exported logs can be stored in your backup system for long-term record keeping or regulatory compliance.
Viewing Detailed Log Entries
Click on any entry in the Activity Logs table to open a detailed view of the user action. This detailed log page provides complete visibility into what was changed, by whom, when, and from where.
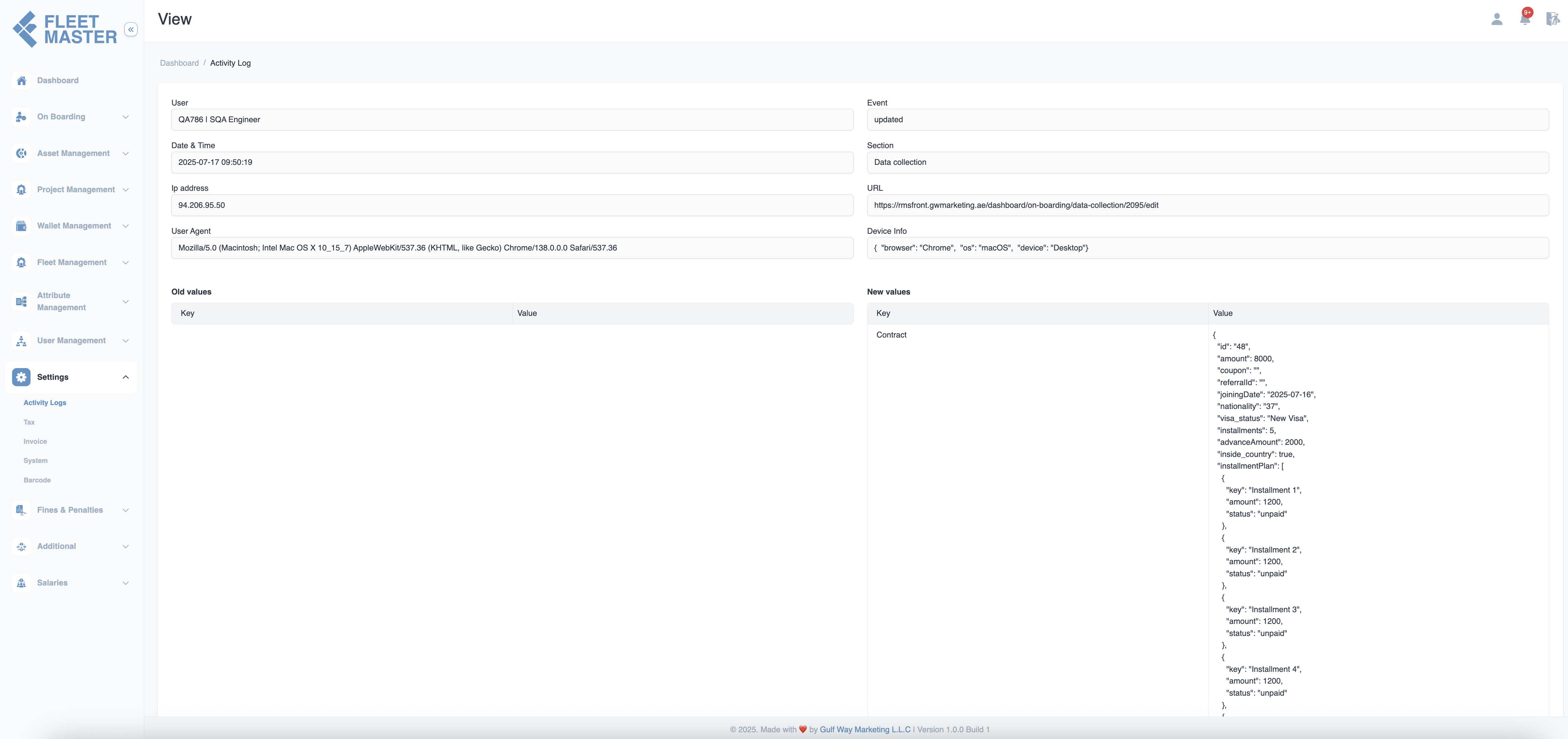
Each activity log detail view includes:
- User: Name and ID of the user who performed the action
- Event: Type of action (Created, Updated, Deleted)
- Date & Time: Exact timestamp of the action
- Section: System module or feature affected (e.g., Vehicle, Admin)
- IP Address: Source IP for traceability
- URL: The system address where the action took place
- User Agent: Device/browser details for advanced audits
- Device Info: Type of device used
- Old Values: What data looked like before the action (for updates/deletes)
- New Values: What data looks like after the action
Change Tracking:
For updated records, compare old values and new values to audit what was changed.
Example
The example below shows a user creating a new vehicle entry in the system:

Audit Use Cases
Track Unauthorized Access
By reviewing IP addresses and timestamps, you can detect any suspicious activity or unauthorized access attempts.
Monitor System Changes
Review actions taken by Admins and Operators, including:
- Created or updated users
- Modified vehicles or roles
- Deleted records or permissions
Troubleshoot Issues
If there's an error or inconsistency in the system, use the logs to trace back the user actions that led to it.
Best Practices
- Review logs daily to monitor critical updates and user behavior.
- Filter by role type (Admin, Vehicle, User) to audit specific team actions.
- Match timestamps and IPs to correlate events with network activity.
Log Retention Policy:
Ensure your organization defines how long logs should be stored and who can access them.